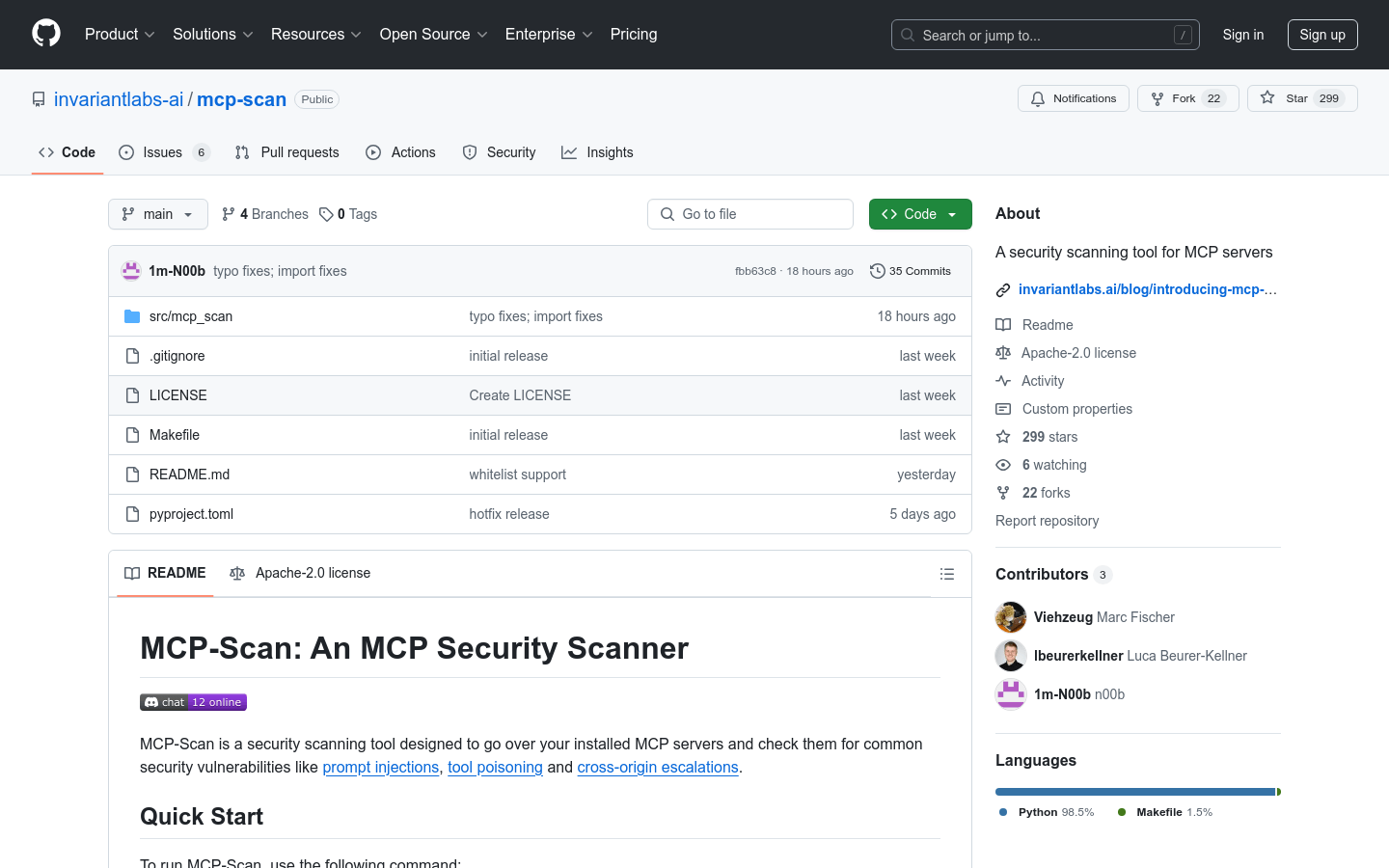
MCP-Scan is a security scanning tool designed specifically for MCP servers that can detect common security vulnerabilities such as prompt injection and tool poisoning. It helps users ensure the security of the system by checking configuration files and tool descriptions. It is suitable for all kinds of developers and system administrators and is an important tool for maintaining system security.
Demand population:
"This product is suitable for developers and system administrators who need to protect their MCP servers from security threats and ensure the security of tools and systems."
Example of usage scenarios:
Developers use MCP-Scan to scan their local MCP servers to ensure there are no security vulnerabilities.
System administrators run MCP-Scan regularly to detect and prevent potential tool poisoning attacks.
Enterprises use MCP-Scan to monitor changes in MCP tools to ensure data integrity and security.
Product Features:
Scan the MCP client configuration in file formats such as Claude, Cursor, Windsurf, etc.
Prompt injection and tool poisoning attacks in the detection tool description
Identify cross-domain upgrade attacks (tool shadow attacks)
Detect changes in MCP tool by hashing to prevent MCP pull-up attacks
Use the command line tool to check the description of installed tools
Tutorials for use:
Install MCP-Scan tool: Install MCP-Scan via pip.
Run the scan command: Use the command 'uvx MCP-Scan @latest' to scan the MCP server.
Specify configuration file: You can specify the location of the MCP configuration file through parameters.
Set scanning options: Set parameters such as the number of checks and timeout as needed.
View scan results: After the scan is completed, check the output results to identify potential security issues.